I may be slightly biased after growing up and being inundated with hackers in movies, (and from working in the cybersecurity industry), but in my mind, ethical hacking is one of the most interesting fields in tech.
It pays well, there’s always something new to learn, and the job itself is like an ongoing strategy game. You’re either learning how to hack into a system to find flaws or figuring out how to stop people from hacking you.
In this guide, I’m going to walk you through the major skills and requirements to become an Ethical Hacker, as well as share how to learn them, and answer some common questions.
So that by the end of this guide, you can start your journey to becoming an Ethical Hacker - even if you’ve never worked with code or computers before!
So grab a coffee and let’s dive in.
Don't feel like reading?:
How to become an Ethical Hacker without a degree!
This process I’m about to share is from our Ethical Hacking career roadmap.
Become a Ethical Hacker & Cybersecurity Expert
15 milestones 12 courses
Step-by-step roadmap where you'll learn to code and build a portfolio.
Curated curriculum of courses, workshops, challenges, projects, and action items.
Become a Ethical Hacker & Cybersecurity Expert from scratch and actually get hired.
Earn on average per year:
$126,653
US salary data collected from Indeed, LinkedIn, and Web3.career 2026.
Feel free to keep reading this guide, as I’ll also give some relevant context as to why you should learn these things in this order.
I’ll also share a running tally of how long each resource takes to learn, based on the average completion time of our students.
So let’s dive into it:
Optional step. Speed up your learning
Because you're going to be learning a lot of new skills, I recommend taking a slight detour and checking out this guide or better still, this course:
Estimated Time Required For This Step: 5.5 hours
It will teach you how how to learn using concepts you've never heard of before.
Why care?
Because it'll help you learn faster, which will then reduce the total time it takes you to learn all these other skills you'll need. (It's kind of like stopping the car to fix a flat tire, because you know it will make the whole journey much quicker and smoother).
Then, once you’ve gone through that course and figured out how to learn faster, you can jump into learning Ethical Hacking at a more accelerated pace.
Step #1. Learn a programming language
Technically, you don’t have to learn a programming language to become an Ethical Hacker, as there are a lot of pre-built tools you can use that do a lot of the work for you.
However, I highly recommend that you learn Python:
Average time to learn: 42 days (although you wouldn't need to complete the full course to grasp the basics).
If you want to be able to hack or defend systems, it’s not a terrible idea to learn the basics of some programming languages right? This is why a lot of companies have Python listed as a required skill in their job posts, even if you never actually write code in your day-to-day work.
A lot of hacking tools use Python for network scanning, port scanning, web application testing, and vulnerability scanning so it's definitely worth learning.
Other than Python, you might also want to learn:
PHP
C and C++
and SQL
Here's why...
PHP
Average time to learn: 42 days
PHP is an older site-building language but it’s used by WordPress which is the building block for over 40% of the internet!
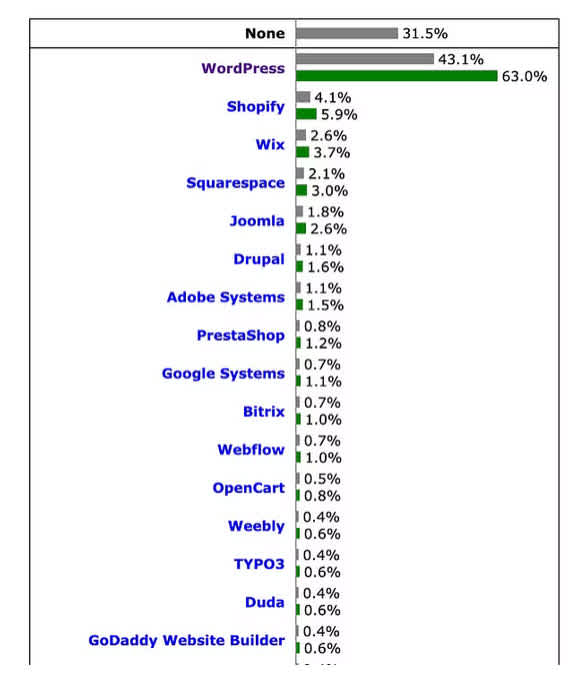
Not only is it worth knowing because you might work with one of these platforms, but hackers can also use PHP to write custom scripts to probe for common vulnerabilities such as SQL injection opportunities (more on this in a second), cross-site scripting, and insecure file uploads.
C and C++
C is commonly used for developing software, operating systems, and embedded software, while C++ is often used for developing large, complex software systems, such as games, graphical applications, and real-time simulations.
Both languages are popular choices for performance-critical applications and are widely used in the tech industry.
In Ethical Hacking though, C and C++ are often used to create exploit code and testing tools, due to their low-level access to hardware, memory, and system resources.
Their speed, efficiency, and control over hardware also make them ideal for developing tools for vulnerability analysis and penetration testing, while their ability to directly manipulate memory and system resources makes it possible to create efficient, low-level exploits that can bypass security measures.
SQL
Average time to learn: 45 days
SQL, or Structured Query Language, is pretty much the backbone of any website that uses some kind of database, be it for products, account numbers, customer information, etc.
By crafting SQL injection attacks, hackers can insert malicious code into an SQL statement, potentially gaining unauthorized access to sensitive data, and even manipulating the database to extract, modify, or delete data.
Which programming language should you learn first as an Ethical Hacker?
Start with Python. It's the easiest to learn, and will help you out the most when starting out.
You can always learn the other programming languages mentioned in this guide later on if you want, or pick up a lot of info on how to utilize their weaknesses as you learn pen testing later.
Again, you ‘technically’ don’t need to learn everything about a language to become a hacker and use it. However, some employers do ask for relevant programming experience, so don’t skip learning Python.
It’ll also help you to form out-of-the-box attacking and defensive techniques.
Step #2. Build a portfolio early
The really cool thing about working in tech, is you don't need a degree to get hired (most of the time). However, you do need to prove you can do the work, and that’s where portfolios come in. You set one up and share your work there so that prospective employers can see what you’ve done and then possibly hire you.
Admittedly at this point, you won't have created any cybersecurity projects, but it’s still worth setting up now and adding to as you go, as its much easier than trying to add it all later. (You always forget to add things otherwise).
And don’t forget, some security roles care about your programming experience so you could add in some Python projects now, and then keep adding as you learn more.
Learn how to set up a portfolio site here, as well as some tips on how to make yourself far more hireable:

Average time to complete: 10 days
Step #3. Learn the core skills for Ethical Hacking
As I mentioned earlier in the intro, there are 2 sides to Ethical Hacking:
Offense aka the hacking side, and
Defense aka trying to stop people from hacking
You can’t really learn one without picking up information about the other, but there are specific details and techniques that are worth learning from both sides of the coin.
With that in mind, start off by learning how to hack, and all that involves, such as:
Linux, Kali Linux, and Virtual Machines (most hacking tools use Linux)
Recon and info-gathering methods
Scanning tools
Vulnerability analysis and opportunities
Exploitation and gaining access (Scripts, Trojans, Viruses, Payloads, Brute force attacks, and Man in the middle exploits
Post-exploitation methods, such as elevating privileges, extracting data, adding keyloggers, and persistence on the system
I actually teach a course that covers all of this:
Average time to complete: 60 days
It’ll walk you through everything you need to know from an offensive perspective, as well as share tools and projects you can build to perform penetration tests.
Want a sneak peek?
Here's the first 4.5 hours of the course that you can watch for free:
Although bare in mind that this video is a little older, and the course is updated multiple times per year.
Step #4. Learn the basics of defensive cybersecurity
A lot of hacking issues can be prevented upfront with good defensive habits, such as:
Knowledge of common threats and bugs
Being aware of and removing common and emerging vulnerabilities
Educating team members on best practices and safety from social engineering
End-point protection, and
You can learn all of these defensive cybersecurity techniques (and more) in this course here:
Average time to complete: 30 days
By learning these alongside hacking skills, you’ll be better at both defense and offense, than you would if you only ever learned the one area of focus.
Step #5. Start applying for Ethical Hacking jobs
Have you been keeping up with your portfolio?
If not, then make sure to add any projects that you made in the last 2 courses (or from other sources), and then start applying for cybersecurity roles now, even if you don’t feel 100% ready yet.
The reason why I recommend this is that:
You’re probably a lot more skilled and knowledgeable than you might think. (We make sure that ZTM students know the most important information and get the best practical experience)
The tech hiring process can sometimes be a lot of applications and interviews before you secure a role, so it's worth starting early while you learn any other 'bonus' skills
I HIGHLY recommend you check out Andrei's course on getting hired at your dream job:
Estimated Time Required For This Step: 12 days.
He covers the entire application and interview process in detail, including with his technique where he gets a 90% interview success rate!
Step #6. Get certified
Because the tech industry is always changing, it means that cybersecurity experts have to stay on top of their game. If you miss a new key exploit in a software update, or fail to understand some emerging tech and your whole system could be at risk.
A great way to stay on top of the broader elements (and get hired at better-paying companies) is to not only take regularly updated training courses but to also take and pass security certification exams. These certifications test you on the most important and latest information, and you can prove to employers that you’re staying on top of everything new.
It’s a win-win situation for both you and employers, and it’s why a few of them ask for these certs in their job descriptions.
There are a few certificates you can take, such as:
CompTIA Security+
GIAC Pen tester (GPEN)
Certified Ethical Hacker (CEH)
And the notoriously difficult Offensive Security Certified Professional (OSCP) which requires you to hack 2 separate systems in 24 hours!
Most companies will be happy with the CompTIA+ certifications, but it’s always best to check the hiring details of your ideal company, and then work towards passing the specific certifications that they want.
They're quite difficult but you can take our course to help you pass them and get your certifications:
Become a CompTIA Certified
7 milestones 5 courses
Step-by-step roadmap where you'll learn to code and build a portfolio.
Curated curriculum of courses, workshops, challenges, projects, and action items.
Become a CompTIA Certified from scratch and actually get hired.
Earn on average per year:
$112,453
US salary data collected from Indeed, LinkedIn, and Web3.career 2026.
Average time to complete: 30 days
Step #7. Increase your skills and income
By this point you should already be hired and working as an Ethical Hacker. However, you could always be making more money!
The easiest way to add in some side income is to apply your pen testing skills to bug bounties, where you try to find flaws in a system for a reward.
In addition to these financial rewards, bug bounty programs can also lead to recognition from the company and the broader Ethical Hacker community. This recognition can sometimes even lead to career opportunities and invitations to exclusive events.
Not bad right, but what about consistently higher salaries?
Well, 2 good channels of focus would be DevOps and A.I...
Learn the impact of A.I on Cybersecurity
A.I tools are not just handy for odd tasks. Hackers are learning how to use these AI tools to improve their hacking efforts.
And if they're learning it, then you need to know this also!
You need to know all this so you can also educate team members so they don't make mistakes, so don't skip this information.
Speaking of A.I. tools though...
Why not learn to use A.I. tools to make your life easier
Although you don't have to do this, I highly recommend that you learn to use AI tools to supplement what you do already.

Average time to complete: 24 days
By learning these skills, you can then increase your output and perform repeatable tasks in minutes vs hours or days, while also making yourself a stand out in interviews.
Learn DevOps for CyberSecurity
This course on Bash Shell scripting will not only teach you how to set up automated scripts (great for hacking), but it’ll also help you to learn everything you need to know to get hired as a DevOps Engineer, SysAdmin, or Network Engineer.
Average time to complete: 20 days
Become an Ethical Hacker today!
Combined running total for all steps to becoming an Ethical Hacker: Just 7 months!
Not bad for a total career change right?
And to be clear, that's how long the average person takes to complete these courses while also working full-time and learning on the side. The course content is much shorter, so if you have more free time, you can get this done much quicker.
That being said, becoming an Ethical Hacker requires dedication, perseverance, and a continuous commitment to learning and growing. Not only do you need to learn cybersecurity, but also need a thorough understanding of other fields in tech so that you can keep them secure.
Personally, I feel like this is one of the main benefits of the industry because you’re always learning something new and growing your skills while getting paid handsomely to do it.
Ready to give it a try?
Every single one of the courses that I’ve shared above is included in a Zero To Mastery Academy membership. So once you join, you have access to all of them, and they’re always up to date with the latest information.
Become a Ethical Hacker & Cybersecurity Expert
15 milestones 12 courses
Step-by-step roadmap where you'll learn to code and build a portfolio.
Curated curriculum of courses, workshops, challenges, projects, and action items.
Become a Ethical Hacker & Cybersecurity Expert from scratch and actually get hired.
Earn on average per year:
$126,653
US salary data collected from Indeed, LinkedIn, and Web3.career 2026.
Not only that, but you have access to our private Discord community where you can ask questions and chat with me, my other students, and working cybersecurity professionals:
Make today the day you invested in yourself and your future, and become an Ethical Hacker today!
Best articles. Best resources. Only for ZTM subscribers.
If you enjoyed this post and want to get more like it in the future, subscribe below. By joining the ZTM community of over 100,000 developers you’ll receive Web Developer Monthly (the fastest growing monthly newsletter for developers) and other exclusive ZTM posts, opportunities and offers.
No spam ever, unsubscribe anytime

![Learning to Learn [Efficient Learning]](https://images.ctfassets.net/aq13lwl6616q/6VWcUgLgG0SU55ORlILe2S/e186361aeb48561bcd19ae6486577022/Learning_to_Learn.jpg?w=600&h=336&fl=progressive&q=50&fm=jpg&bg=transparent)













