In This Guide:
- What is Ethical Hacking?
- What does an Ethical Hacker do?
- Are Ethical Hackers in demand?
- How much can you earn as an Ethical Hacker?
- Do I need a degree to become an Ethical Hacker?
- What skills do I need to become an Ethical Hacker?
- How long does it take to become an Ethical Hacker?
- How to become an Ethical Hacker (Without a degree!)
- Step #1: Set yourself up for success
- Step #2: Learn a programming language (Python)
- Step #3: Build a portfolio early
- Step #4: Learn the basics of Ethical Hacking
- Step #5: Learn the basics of defensive cybersecurity
- Step #6: Start applying for cyber security jobs
- Step #7: Get certified (CompTIA+ or others)
- Step #8: Increase your skills and income!
- So what are you waiting for? Become an Ethical Hacker today!
I may be slightly biased after growing up in the 90s and being inundated with hackers in movies, (and from working in the industry), but in my mind, ethical hacking is one of the most interesting fields in tech.
It pays well, there’s always something new to learn, and the job itself is like an ongoing strategy game. You’re either learning how to hack into a system to find flaws or figuring out how to stop people from hacking you.
In this guide, I’m going to walk you through the major skills and requirements to become an Ethical Hacker, share how to learn them, while also answering some common questions.
So that by the end of this guide, you can start your journey to becoming an Ethical Hacker - even if you’ve never worked with code or computers before!
So grab a coffee and let’s dive in.
Don't feel like reading?: Check out the video version below:
What is Ethical Hacking?
Ethical hacking is the practice of intentionally accessing or ‘penetrating’ systems and networks to find and fix security vulnerabilities. Its purpose is to help organizations improve their security measures by identifying weaknesses before malicious hackers can exploit them.
This proactive approach can save companies from potential data breaches, financial loss, and damage to their reputation.
It’s also more effective than most passive methods because it mimics the tactics of real attackers, such as social engineering, whaling, phishing and more.
What does an Ethical Hacker do?
There are 4 main elements to this role:
- You stay on top of industry trends and certifications. This way you can be aware of new system flaws and techniques that malicious hackers might use. You also continue to learn or stay on top of relevant technology and languages in that company toolkit
- You assess the vulnerability of a system. By performing recon on the system and its users
- Then, you attempt to hack the system using multiple methods and processes. This involves exploiting flaws and working towards gaining further access
- Finally, you present your findings and advice for how to remove the issue, or upgrade security. That being said, you might even make the company you are testing aware of a serious flaw immediately during your test
Now although there are 4 main elements, some people may choose to specialize in certain areas.
For example
Cyber Security analysts focus on assessing their systems and improving their defenses, but they don’t usually try to hack the system.
Whereas a penetration tester's main role is to try and get in. They only really care about defense when advising the client what needs improving.
Are Ethical Hackers in demand?
They sure are! According to the US Bureau of Labor Statistics, information security roles are expected to increase 32% by 2032, which is way above the average growth curve for most industries.
Why such demand?
Simply because almost everything is online nowadays, and it continues to trend that way. Everything from apps to smart cars needs cybersecurity, and companies are actively looking to hire.
In fact, at the time of writing this post, there are over 56,000 open Cyber Security roles in the US alone.
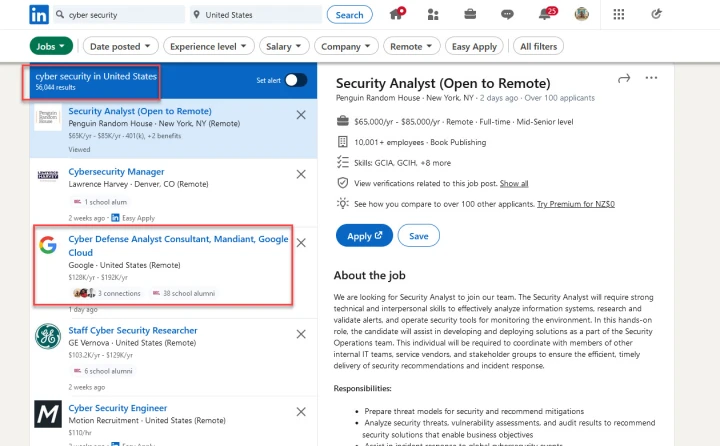
$192k a year to assist with cybersecurity at Google… not bad!
It’s not just Fortune 500s and startups that need cyber security though. Industries such as finance, healthcare, and government agencies, all have a heightened need for Ethical Hackers to safeguard sensitive information and prevent cyber attacks.
If these stats don't convince you, then I don't know what will:
- There is a hacker attack every 39 seconds
- 64% of companies have experienced web-based attacks
- Since COVID-19, the US FBI reported a 300% increase in reported cybercrimes
- ~$10.5 trillion is expected to be spent globally on cybersecurity by 2025
Demand is already high and growing, and the pay is pretty good also…
How much can you earn as an Ethical Hacker?
Like all areas in tech (and pretty much any job) your potential earnings all depend on your level of experience, skillset, and geographic location.
For example
If you’re in a capital city and working with the government, working in a high-demand industry like Fintech, or if you’re in Silicon Valley and working with FAANG or similar large Enterprise company, then your salary range can be much higher.
Likewise, as you add more specific skills in niche areas of cybersecurity, such as mobile security, cloud security, or IoT security then your salary can increase again.
The role I shared earlier was $192,000 (at the top end of the range) plus benefits and stock options.
Although this role requires a specialized skill set and a lot of relevant experience, it’s not even a senior position, which could pay even more.
So what about non-FAANG salary ranges?
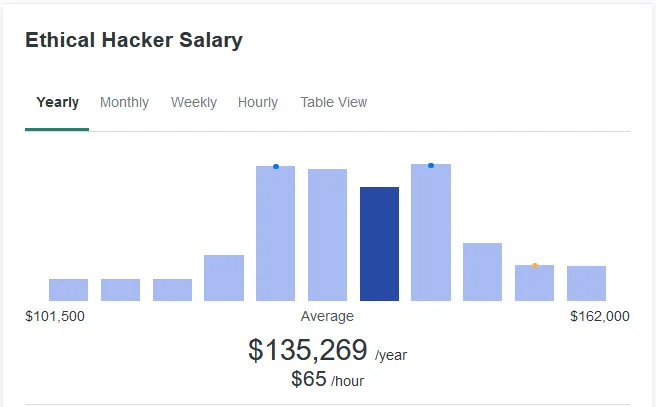
If we take a look at ZipRecruiter, then the average salary for Ethical Hacker jobs on their site right now is around $135,000, with jobs ranging from $101,500 - $162,000.
Do I need a degree to become an Ethical Hacker?
Nope! It might help if you understand some of the core principles that are covered in CS degrees, but there’s nothing stopping you from learning those skills from a course or bootcamp.
A lot of tech roles are like this. They care more that you have relevant experience and a portfolio of projects than anything else.
In fact, if we look at that Google role again, at no point does it ask for a degree.
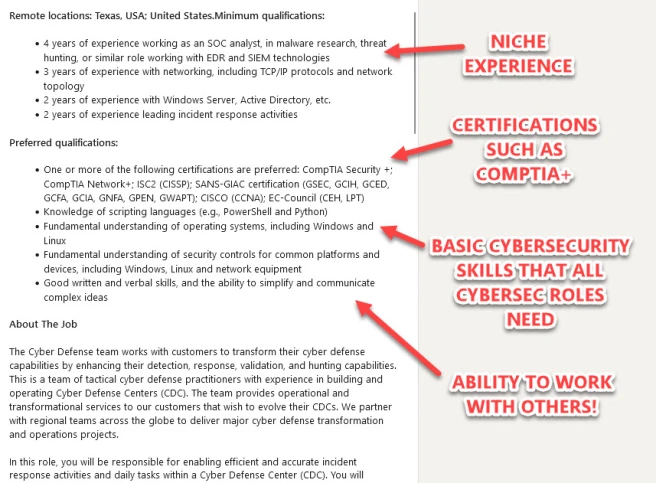
All they care about is some of the skills we’re about to recommend 😉.
What skills do I need to become an Ethical Hacker?
I'll go through these in more detail as we go through the roadmap, but here's a mile high view of each of the most important skills you'll need for this role:
- Communication Skills: Because you'll be working with both tech and non-tech stakeholders or clients, you need to be able to effectively communicate findings and recommendations in a way that everyone can understand. Why is this threat important and what do they need to do about it?
- Continuous Learning: The field of cybersecurity is constantly evolving, so a commitment to continuous learning and staying updated on the latest threats, tools, and techniques is essential. I actually think this is one of the main benefits of the role, in that it's always changing which means you get to keep learning new things!
- Critical Thinking and Problem-Solving Skills: Ethical hackers need to think creatively to identify vulnerabilities and develop effective solutions to mitigate them. Because programs and platforms change, new ideas for attacking or defending them are needed
- Security Fundamentals: You need to know the basics of cybersecurity defense, which means an understanding of security concepts such as encryption, authentication, access control, and common vulnerabilities like buffer overflows, SQL injection, XSS, etc
- Cybersecurity Laws and Ethics: Knowledge of relevant laws, regulations, and ethical guidelines governing cybersecurity and hacking activities is necessary to ensure you operate within legal and ethical boundaries. You don't want to do something illegal by accident!
- Penetration Testing Tools: You also need to understand the offensive side of cybersecurity. This means you need to not only know, but be proficient with tools like Metasploit, Nmap, Wireshark, Burp Suite, and others
- Programming Skills: Competency in programming languages such as Python, or scripting languages like PowerShell and Bash will help you automate tasks, develop tools, and understand vulnerabilities
- Web Application Knowledge: Familiarity with web technologies (HTML, CSS, JavaScript, PHP, etc.) and web application architecture is essential for assessing and securing web applications. A lot of the time, it's easy exploits that pass through
- Operating System Knowledge: Likewise, you need to be proficient and understand operating systems like Windows, Linux, and Unix is essential, as most systems you'll encounter will be based on these platforms
- Understanding of Networking: Finally, a knowledge of how networks function, including protocols, IP addressing, routing, and subnetting, is crucial for understanding vulnerabilities and potential attack vectors
Each of these areas is vital to be an effective Ethical Hacker. Like I said earlier though, I'll go into all of these in more detail in the roadmap in just a second.
Also, don't freak out if this seems like a lot to learn. A good Ethical Hacking course will teach you all of this as you go, so it won't be as overwhelming.
How long does it take to become an Ethical Hacker?
Again, this depends on the level that you want to achieve. For the most basic junior position, you can easily learn this in 3-6 months, or faster. (I’ll share some resources and time frames in just a second).
For more senior or niche roles, you’ll also have to acquire specific skills and then build up some years of experience.
I recommend that you learn what you need to get started at a basic level and start working ASAP, and then continue to skill up so you can then move into higher paying positions.
Here’s how…
How to become an Ethical Hacker (Without a degree!)
This process I’m about to share is from our Ethical Hacking career roadmap.
Feel free to keep reading this guide, as I’ll also give some relevant context as to why you should learn these things in this order.
I’ll also share a running tally of how long each resource takes to learn, so let’s dive into it:
Step #1: Set yourself up for success
This first step is completely optional but highly recommended, because here’s the thing: Most people don’t know how to learn effectively.
It’s not their fault. Schools teach basic rote methods of learning which are pretty inefficient. They say the thing, and you try to remember the thing, and it's not great - especially if you require certain learning styles to learn best.
This means that topics you might do well with are harder to remember or apply, so it takes longer to learn.
The thing is, there are multiple different learning techniques that you can use that make all of your future learning efforts far more effective. This means you can understand faster and more efficiently, so less back and forth.
You can learn a lot of the key techniques for free right now in this guide, or better still, watch every important technique inside of Andrei’s learning how to learn course.
Estimated Time Required For This Step: 5 days.
I know it might feel like a step backward or even a detour, but think about it like this:
- You can learn the core principles in a few days and then immediately start putting them into practice
- You're going to learn everything else from now on 2x faster and retain way more as well
- This is a skill that you can keep developing over time and will serve you for your entire career, guaranteed
Bear in mind that there are multiple skills that you need to pick up to become an Ethical Hacker, and each of them can take weeks or even months of work to complete.
So why not learn how to cut down on that time, improve your comprehension, and pick up skills faster and easier first? The time and energy savings will seriously compound as you go through the rest of the content you need to learn.
Then, once you’ve gone through that course and figured out how to learn faster, you can jump into learning Ethical Hacking at a more accelerated pace.
Step #2: Learn a programming language (Python)
Technically, you don’t have to learn a programming language to become an Ethical Hacker, as there are a lot of pre-built tools you can use that do a lot of the work for you.
However, I highly recommend that you learn a programming language.
Why?
For three reasons:
- Underlying knowledge gaps
- Improved job opportunities, and
- Additional applied knowledge for hacking and whitebox testing
If you want to be able to hack or defend systems, it’s not a terrible idea to learn the basics of some programming languages right?
This is why a lot of companies have Python (and a few other languages) listed as a required skill in their job posts, even if you never actually write code in your day-to-day work.
Trust me when I say that it's worth learning - even if you struggle at first. At the very least, if you learn to code, you'll also stand out when you apply for posts that don't request it.
Finally, learning to code will also give you outside the box thinking skills, as well as additional underlying technical and system knowledge.
For example
These languages can be used for specific hacking techniques and tools, or to leverage vulnerabilities.
PHP
Average time to learn: 42 days
PHP is an older site-building language but it’s used by WordPress which hosts over 40% of the internet.
Hackers can use PHP to write custom scripts to probe for common vulnerabilities such as SQL injection opportunities (more on this in a second), cross-site scripting, and insecure file uploads.
C and C++
C is commonly used for developing system software, operating systems, and embedded software, while C++ is often used for developing large, complex software systems, such as games, graphical applications, and real-time simulations.
Both languages are popular choices for performance-critical applications and are widely used in the tech industry.
In Ethical Hacking though, C and C++ are often used to create exploit code and testing tools, due to their low-level access to hardware, memory, and system resources.
Their speed, efficiency, and control over hardware also make them ideal for developing tools for vulnerability analysis and penetration testing, while their ability to directly manipulate memory and system resources makes it possible to create efficient, low-level exploits that can bypass security measures.
SQL
Average time to learn: 45 days
SQL, or Structured Query Language, is pretty much the backbone of any website that uses some kind of database, be it for products, account numbers, customer information, etc.
By crafting SQL injection attacks, hackers can insert malicious code into an SQL statement, potentially gaining unauthorized access to sensitive data, and even manipulating the database to extract, modify, or delete data.
Python
Average time to learn: 60 days
Python is not only an easy-to-use scripting language, but a lot of hacking tools use it for network scanning, port scanning, web application testing, and vulnerability scanning.
Its widespread use, coupled with its flexibility and power, make Python an ideal choice for penetration testing tasks, allowing Ethical Hackers to perform a range of essential functions with ease and efficiency.
It’s also an amazing first programming language to learn for beginners. That’s why out of all the potential programming languages you could learn, I recommend you learn Python as the first step in your Ethical Hacking journey.
Which programming language should you learn first as an Ethical Hacker?
Start with Python. It's the easiest to learn, and will help you out the most when starting out.
You can always learn the other programming languages mentioned in this guide later on if you want, or pick up a lot of info on how to utilize their weaknesses as you learn pen testing later.
Again, you ‘technically’ don’t need to learn everything about a language to become a hacker and use it. However, some employers do ask for relevant programming experience, so don’t skip learning Python.
It’ll also help you to form out-of-the-box attacking and defensive techniques.
Step #3: Build a portfolio early
Remember how I said earlier that tech cares more about proving you can do something, vs having a degree? Well, that’s where portfolios come in.
You set one up and share your work there so that prospective employers can see what you’ve done and then possibly hire you.
Admittedly at this point, you won't have created any cybersecurity projects, but it’s still worth setting up now and adding to as you go, versus trying to add it all later. (You always forget to add things otherwise).
And don’t forget, some security roles care about your programming experience so you could add in some Python projects now, and then keep adding as you learn more.
Learn how to set up a portfolio site here, along with types on how to make yourself far more hirable.
Average time to complete: 10 days
Step #4: Learn the basics of Ethical Hacking
As I mentioned earlier, there are 2 sides to Ethical Hacking:
- Offense aka the hacking side, and
- Defense aka trying to stop people from hacking
You can’t really learn one without picking up information about the other, but there are specific details and techniques that are worth learning from both sides of the coin.
With that in mind, start off by learning how to hack, and all that involves, such as:
- Linux, Kali Linux, and Virtual Machines (most hacking tools use Linux)
- Recon and info-gathering methods
- Scanning tools
- Vulnerability analysis and opportunities
- Exploitation and gaining access (Scripts, Trojans, Viruses, Payloads, Brute force attacks, and Man in the middle exploits
- Post-exploitation methods, such as elevating privileges, extracting data, adding keyloggers, and persistence on the system
How cool does that all sound!? It’s like you’re some kind of spy from the comfort of your desk!
Check out our complete Ethical Hacking course here.
Average time to complete: 60 days
It’ll walk you through everything you need to know from an offensive perspective, as well as share tools and projects you can build to perform penetration tests.
Want a sneak peek?
Take my crash course below, completely for free!
You'll learn the basics and fundamentals of hacking including Linux and Linux Terminal, setting up your hacking environment (Kali Linux and Virtual Machines), the 5 phases of penetration testing, how to do reconnaissance and scanning, and much more!
This will give you a grant chance to see if this is a career you're interested in and if you are, you can get going deeper with my full Ethical Hacking Bootcamp.
Back to the guide...
So far, we’re around 4 months in. In theory, you could apply for some junior-level cybersecurity roles right now and start getting paid, but let’s keep going.
Step #5: Learn the basics of defensive cybersecurity
A lot of hacking issues can be prevented upfront with good defensive habits, such as:
- Knowledge of common threats and bugs
- Being aware of and removing common and emerging vulnerabilities
- Educating team members on best practices and safety from social engineering
- End-point protection, and
- Network security
By learning these alongside hacking skills, you’ll be better at both defense and offense, than you would if you only ever learned the one area of focus.
Average time to complete: 30 days
You can learn all of these defensive cybersecurity techniques (and more) in this course here.
Step #6: Start applying for cyber security jobs
Have you been keeping up with your portfolio?
Make sure to add any projects that you made in the last 2 courses (or from other sources), and then start applying for cybersecurity roles now - even if you don’t feel 100% ready yet.
The reason why I recommend this is that:
- You’re probably a lot more skilled and knowledgeable than you might think (We make sure that ZTM students know the most important information and get the best practical experience)
- And tech can sometimes be a lot of applications and interviews before you secure a role
If you're a ZTM member, then I HIGHLY recommend you check our Andrei's new course on getting hired at your dream job:
Estimated Time Required For This Step: 12 days.
He covers all this in far more detail, including his technique to get a 90% interview success rate!
If you're not a ZTM member, then check out this guide, as well as these extra tips:
Tech jobs are more than just tech skills
In addition to the technical know-how that you’ve built up through education and certification, interviewers will be evaluating your soft skills.
- Be prepared with examples showing how you’ve collaborated with co-workers or led teams or projects in the past
- Make sure to demonstrate strong communication skills in writing and during the interviews (whether virtual or in-person)... Even very basic things like using proper grammar and having no spelling mistakes, sending a thank you email within 24 hours of your interview, etc
Have specific examples of how you’ve solved problems
A Ethical Hacker does a lot of troubleshooting and problem solving. Either to find a way to hack, or to figure out HOW you've beend hacked.
Problem solving skills are key, so:
- Be prepared to talk through a situation or two where you saved the day by solving a complex or business-critical problem
- If you don’t have work-related examples, share stories from school or community projects
Make sure to do the usual interview prep
Like any other kind of interview, it’s always good to:
- Research the company. Learn what you can about their needs and why they’re hiring for your role
- Learn what you can about the people you’ll be interviewing with, and what their potential areas of focus will be. You can always ask when they offer the interview, and they will happily let you know
- Practice, practice, practice. Do a mock interview with friends or family, or even just interview yourself, speaking your answers out loud. It’s amazing the difference this makes, and how much more polished you’ll be on the big day
Be on time (or even a little bit early) for the interview Dress the part. Figure out the “norm” for the company’s culture (jeans and T-shirt or more professional?) and dress to fit in. If you’re unsure, err on the side of dressing “up". Dressing like Neo might get a laugh but probably not the job!
Do all this, and you’ll smash the interview and get the hired.
Step #7: Get certified (CompTIA+ or others)
Because the tech industry is always changing, it means that cybersecurity experts have to stay on top of their game. Miss a key exploit in a software update, or fail to understand an emerging tech and your whole system could be at risk.
A great way to stay on top of the broader elements (and get hired at better-paying companies) is to not only take regularly updated training courses but to also take and pass security certification exams.
These certifications test you on the most important and latest information, and you can prove to employers that you’re staying on top of everything new.
It’s a win-win situation for both you and employers, and it’s why a few of them ask for these certs in their job descriptions.
There are a few certificates you can take, such as:
- CompTIA Security+
- GIAC Pen tester (GPEN)
- Certified Ethical Hacker (CEH)
- And the notoriously difficult Offensive Security Certified Professional (OSCP) which requires you to hack 2 separate systems in 24 hours!
Most companies will be happy with the CompTIA+ certification, but it’s always best to check the hiring details of your ideal company and then work towards passing those certifications.
I’ll be totally honest - they’re not the easiest thing to pass, but you can always take refresher courses in advance to help you with them.
Speaking of which, you can learn how to pass the CompTIA+ here.
Average time to complete: 30 days
Running total: 6 months
By now you have enough skills to apply for most entry and mid-level cybersecurity roles, and could easily start applying for those $100k a year Ethical Hacker roles that we saw on ZipRecruiter.
Step #8: Increase your skills and income!
By this point you should already be hired and working as an Ethical Hacker. However, you could always be making more money!
The easiest way to add in some side income is to apply your pen testing skills to bug bounties, where you try to find flaws in a system for a reward. (With some rewards being mid 5-6 figures or higher!).
In addition to these financial rewards, bug bounty programs can also lead to recognition from the company and the broader Ethical Hacker community. This recognition can sometimes even lead to career opportunities and invitations to exclusive events.
Not bad right, but what about consistently higher salaries?
Well, 2 good channels of focus would be DevOps and A.I...
Learn the impact of A.I on Cybersecurity
A.I tools are not just handy for odd tasks. Hackers are learning how to use these tools (+ more niche AI ones) to improve their hacking efforts.
You know what that means right? If they're learning it, then you need to know this also!
This course on A.I and Cybersecurity will help you learn the vulnerabilities and security risks associated with LLMs and other machine learning models.
Because that's the other thing. It's incredibly easy to add sensitive data inside these tools by accident and think that it's secure, when in reality, it could be viewed by others. (It's also why Data Engineers and even Data Analysts should also learn the basics of Cyber Security). The last thing you want is people sharing sensitive data or access.
You need to know all this so you can also educate team members so they don't make mistakes, so don't skip this information.
Speaking of A.I. tools though...
Why not learn to use A.I. tools to make your life easier
Although you don't have to do this, I highly recommend that you learn to use AI tools to supplement what you do already.
You don't need to work solely with A.I. to see the benefit either. By learning to use these tools, you can increase your output and perform repeatable tasks in minutes vs hours or days.
And sure - the tools are not perfect. You still need to have the core knowledge that you're learned above, but by then applying that experience you have now, with that automation, you'll not only make your life easier - but even grow indemand.
A.I. won't steal your job. But people who can do their job faster and more effectively because they can use the tools, are going to be in high demand.
So add it to you skills, make work easier, and be the one that employers fight over!
We have a few courses on this that you can check out:
- AI for Beginners: Inside Large Language Models
- Prompt Engineering with LLMs
- How the ChatGPT code interpreter works and how to use it
- A.I. coding with GitHub co-pilot
Check those out and see how they can help you.
Also, depending on the time that you read this, there may be new specific A.I. tools for your role, so have a quick Google search and see if there anything that can help, and play around with it.
DevOps For CyberSecurity
This course on Bash Shell scripting will not only teach you how to set up automated scripts (great for hacking), but it’ll also help you to learn everything you need to know to get hired as a DevOps Engineer, SysAdmin, or Network Engineer.
Average time to complete: 20 days
Combined running total for all steps to becoming an Ethical Hacker: 7 months!
Not bad for a total career change right?
So what are you waiting for? Become an Ethical Hacker today!
Becoming an Ethical Hacker requires dedication, perseverance, and a continuous commitment to learning and growing.
Not only do you need to learn cybersecurity, but also need a thorough understanding of other fields in tech so that you can keep them secure.
Personally, I feel like this is one of the main benefits of the industry. You’re always learning something new and growing your skills while getting paid handsomely to do it.
Why not give it a try? The path I shared above will walk you through every step, even if you’ve never written a single line of code before.
You simply start at the beginning and work your way through it, until you succeed - you just need to do the work!
Good news?
Every single one of the courses that I’ve shared is included in the Zero To Mastery Academy. Once you join, you have access to all of them, and they’re always up to date with the latest information.
Not only that, but you have access to all me, my other students, and working cybersecurity professionals inside of our private community, so you can ask questions and get actual experienced feedback.
Make today the day you invested in yourself and your future. Become an Ethical Hacker... starting now!
Want more Cyber Security content?
If you enjoyed this roadmap and want to learn more, then check out my other guides and tutorials!
- Active vs. Passive Reconnaissance in Cyber Security
- Beginner’s Guide to CNAP in Cyber Security
- Beginner’s Guide To Whaling Phishing Attacks
- Introduction to Whitebox Testing in Cyber Security
- A Beginners Guide To Computer Networking
- SOC Analysts: What Are They And How Do You Become One?
- How to Become an Ethical Hacker & Get Hired in 2025
- Cybersecurity Practice Projects For Beginners
- The 5-Step Process To Ethical Hacking
- Complete Guide to the CompTIA Security+ Certification
- Red Team vs Blue Team in Cyber Security
- Sure You Haven't Been Hacked? 3 Steps To Secure Your PC
- How To Find Rootkits On Your Linux Device
- Top 5 Reasons To Learn Cyber Security