You’ve probably heard terms like IDS and IPS mentioned in Cyber Security. Maybe you’ve even seen them listed in job descriptions or setup guides. But what are they really, and why do they matter so much?
If you’re just starting to explore how networks stay protected, understanding these two tools can make a big difference. They sound alike, often show up together, and play a key role in how teams handle threats.
In this guide, you’ll get a clear picture of what they are, how they work, and why they’re so often talked about in the same breath. No jargon. No assumptions. Just a straight explanation that makes sense.
Sidenote: If you want to learn how to take your network security to the next level, then you need to learn how it's hacked in my Network Hacking + Security course:
This course takes your ethical hacking and penetration testing skills to the next level by diving deep into advanced network attacks, showing you how to bypass security measures, exploit vulnerabilities, and even craft your own network-based exploits. The best way to learn to defend, is to understand how the attacks work.
With that out of the way, let’s get into this guide…
What is an Intrusion Prevention System (IPS)?
An IPS is your network’s automatic bodyguard. Instead of just sounding the alarm when something looks off, it steps in and blocks the threat on the spot.
For example
If someone starts brute-forcing your login form, an IPS can spot the pattern and block the attacker before they even finish their second guess.
This setup is ideal for systems that need to react quickly, like public-facing login portals, APIs, or websites, and you’ll usually find an IPS sitting in line with your traffic.
That means every packet and every request coming in or going out passes through it, so that it can block malicious activity in real time. If it sees something dangerous, it can shut down the connection, drop the packet, or stop the request entirely.
However, that speed and power come with a catch.
Because it’s placed directly in the traffic path, the IPS has to be fast, accurate, and tuned properly, because if its slow or if it misidentifies something as malicious then it could block legitimate traffic.
That might mean a user can’t access your service, or worse, your own internal systems could get cut off. (Imagine pushing an internal update and suddenly getting locked out of production because the IPS didn’t recognize the new deployment behavior!)
That’s why many teams start by running IPS tools in monitoring mode at first so they can see what the IPS would block without actually blocking anything. Once the detection rules are fine-tuned and you’re confident in how it’s behaving, only then do they flip the switch to let it act automatically.
How detection works with an IPS
Detection itself happens in a few ways:
Signature-based detection looks for known patterns of attack. It’s fast and reliable for well-documented threats, like specific malware payloads or exploit kits
Anomaly-based detection watches for behavior that breaks from the norm, such as when a server suddenly starts sending out large volumes of data to an unknown IP. It’s useful for catching novel attacks but more likely to flag harmless behavior by mistake. (That being said, some sneaky tools will mimic normal usage on purpose to get around this)
Policy-based detection lets you define your own rules. For example, you might block all inbound SSH traffic from outside your network or limit certain API endpoints to internal IPs only
Many IPS tools combine all three methods, with products like Cisco Firepower or Palo Alto Threat Prevention offer this out of the box.

Others, like Suricata or Snort, can be configured to act like an IPS if placed in-line with the right rules in place.
TL;DR
The real strength of IPS is that it takes pressure off your team when time is critical. If a known threat shows up, the system doesn’t wait for approval. It just acts.
But to work well, it needs to be set up carefully. A poorly tuned IPS can create outages by blocking the wrong traffic. That’s the tradeoff—you get automated protection, but you have to earn it through testing, rule refinement, and a deep understanding of what “normal” looks like in your environment.
But what about the attacks that get past your IPS, or the subtle signs something isn’t right? That’s where IDS comes in.
What is an Intrusion Detection System (IDS)?
An intrusion detection system, or IDS, doesn’t block threats. Instead, it observes them so you or your team can investigate further. Its job is to monitor network traffic and alert you when something looks suspicious.
You can kind of think of it like modern security camera systems. Designed to watch and alert but without directly intervening.
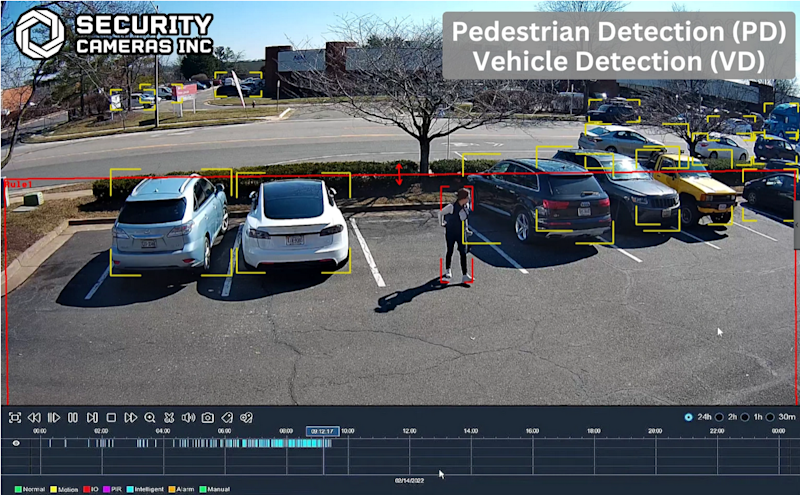
It won’t stop someone from walking through the door, but it will flag them once they’re inside.
That makes IDS especially useful for spotting things your firewall or IPS might miss, such as strange behavior inside your network, or attacks that don’t match known patterns (or intentionally mimic them normal usage).
Basically, an IDS gives you broader visibility without interfering with the actual flow of data.
Speaking of which...
Where IDS fits in your setup
Unlike an IPS, which sits directly in the flow of traffic, an IDS is usually placed out of band. It watches a copy of the network traffic instead of sitting in the direct path. That means it won’t slow down your systems or accidentally block something critical.
For example
Let’s say an attacker has already gotten access to an internal machine and is trying to move laterally, and accessing other systems or escalating privileges. Your IDS can detect unusual login behavior, strange file transfers, or spikes in traffic between internal devices. That kind of activity might not match any known signature but could still be a red flag.
And because it’s not in-line, an IDS won’t get in the way. There’s no risk of it introducing latency or accidentally breaking something your team depends on. That makes it a safe choice in environments where uptime is critical.
How detection works with an IDS
IDS tools use two core methods to spot suspicious activity:
Signature-based detection checks traffic against a database of known threats. It’s fast and precise, but only works if the attack has been seen before
Anomaly-based detection watches for behavior that doesn’t match the baseline of normal activity. It’s useful for catching new or evolving attacks but tends to be noisier and requires tuning to avoid false positives
Both methods have their place. Signature-based detection is great for known malware or specific attack vectors. Anomaly detection is better for zero-day threats or spotting when something just feels off.
But there’s a balance to strike. Too sensitive, and you’ll drown in alerts that don’t matter. Not sensitive enough, and you might miss something real. That’s why tuning your IDS is just as important as setting it up in the first place.
IDS t
Some of the most widely used IDS tools include:
Snort – A well-known open-source tool, also used as an IPS depending on configuration
Zeek (formerly Bro) – Great for deep traffic analysis and scripting custom detections
Suricata – Can run as an IDS or IPS depending on your setup. Often used in high-performance environments
As you'll notice, some of these overlap and perform both roles of IDS and IPS. There's a reason for this but I'll cover it in a second.
TL;DR
The value of an IDS isn’t just about spotting attacks — it’s about context.
Let’s say you get an alert that a user account accessed a file they’ve never touched before, at 3 a.m., from a location they’ve never logged in from. That might not trigger a firewall rule, and an IPS might not block it if it doesn’t match a known pattern. But an IDS can flag it and give your team a chance to investigate before anything gets worse.
That’s why many teams rely on IDS as a core part of their detection strategy. It doesn’t act for you, but it helps you make smarter decisions, faster.
IDS vs IPS: Mile high comparison
So now that you’ve seen what each system does in practice, let’s zoom out for a second. Here’s a side-by-side look at how IDS and IPS compare.
Feature | IDS (Intrusion Detection System) | IPS (Intrusion Prevention System) |
|---|---|---|
Primary function | Monitors and alerts on suspicious activity | Actively blocks threats in real time |
Traffic placement | Out of band (monitors a copy of traffic) | In line (analyzes and filters live traffic) |
Response behavior | Passive (no blocking) | Active (automated blocking and mitigation) |
Risk of disruptions | Low (no interference with traffic) | Inline so medium to high if misconfigured |
False positives impact | Can cause alert fatigue | Can block legitimate traffic |
Best use case | Internal monitoring, post-breach visibility | Perimeter defense, public-facing systems |
Custom rule tuning needed? | Yes | Yes |
Detection methods used | Signature-based and anomaly-based | Signature-based, anomaly-based, policy-based |
Human intervention required? | Yes | Not always — acts automatically based on your settings |
Tool examples | Snort, Zeek, Suricata (in detection mode) | Cisco Firepower, Palo Alto Threat Prevention, Suricata (inline mode) |
Common mistakes and best practices
Even with great tools, it’s easy to get tripped up if they’re not set up or managed well. Here are the main common mistakes that people struggle with when using these tools.
1. Turning them on without tuning them
Like all tools, both IDS and IPS need to be tuned and set up properly before they’re effective. An IPS with loose rules might miss real threats, while one that’s too strict could take down services without warning. IDS can flood you with alerts if it isn’t tailored to your environment.
This is why you should always start in monitoring mode. Review what would’ve been flagged or blocked. Then gradually refine the rules until you’re confident enough to go live.
2. Leaving default rules untouched
Out-of-the-box rules are just a starting point. If you don’t customize them, you’re likely to miss attacks that are specific to your setup—or end up drowning in false positives.
For example
If your dev team regularly pushes large updates at midnight, and your IDS is set to flag high traffic during off-hours, you’re going to get a lot of noise. That’s a clue your baseline needs adjusting.
3. Relying only on signature detection
Signature detection is great for known threats, but today’s attacks change quickly. If you don’t also use anomaly or behavior-based detection, you’ll miss more subtle or novel threats.
This is why you need to mix detection strategies. Signatures are fast and reliable, but anomalies help you catch what isn’t yet in a database.
4. Not integrating with your workflow
It’s not enough to detect something. The alert needs to reach someone who can act on it.
If your IDS or IPS doesn’t feed into your SIEM, ticketing system, or incident response process, it might as well not be there. (alerts are pointless if none is checking and dealing with them right!?).
So always make sure alerts flow into the systems your team already uses, so they actually trigger investigations and responses.
It's not about IPS vs IDS (it's about using both effectively together)
So as you’ve seen, IDS and IPS aren’t interchangeable—and it’s not about picking one over the other. Each plays a different role in your network security strategy, and to build real protection, you’ll want both.
An IPS is your first responder. It blocks threats in real time, making it essential for public-facing systems or anything that can’t afford a delay
An IDS, on the other hand, gives you deep visibility. It helps you spot unusual behavior, understand what’s going on behind the scenes, and make smarter decisions before things escalate
That’s why most teams use both, and it’s why tools like Suricata and Snort offer both modes. You can start in detection mode, tune your rules, and then shift to prevention once you’re confident.
If you’re just getting started, don’t overthink it. Pick a tool that supports both IDS and IPS. Run it in passive mode, see what it catches, and adjust. That real-world testing is where the learning sticks, and where good defenses begin.
P.S.
Remember, if you want to learn how to fully defend your network, then you need to learn how hackers attack them.
So check out my Network Security + Hacking course to learn more.
Take your ethical hacking skills to the next level by learning network hacking techniques, from Man In The Middle and DNS spoofing to router exploits and custom payload creation.
You’ll learn to master real-world attack methods, bypass security measures, and gain the skills needed for penetration testing and cybersecurity roles. Because the best defence understands the offence!
Better still?
If you join ZTM as a member, then you’ll get access to each of my cyber security courses, as well as access to our private Discord server.
Here you can chat to me, other students, and working cybersecurity professionals and get help with any questions you might have 24/7.
It’s the best investment you can make to improve your cyber security in 2025.
Want more Cyber Security content?
If you enjoyed this post, then check out my other guides and tutorials!
Best articles. Best resources. Only for ZTM subscribers.
If you enjoyed this post and want to get more like it in the future, subscribe below. By joining the ZTM community of over 100,000 developers you’ll receive Web Developer Monthly (the fastest growing monthly newsletter for developers) and other exclusive ZTM posts, opportunities and offers.
No spam ever, unsubscribe anytime








